There are several ways to integrate Lacework with accounts in an AWS Organization. Lacework provides multiple Terraform modules for this purpose. In this post, we will focus on the aws_org_configuration module.
Integration:
The aws_org_configuration module offers seamless automation for integrating Lacework with AWS Configuration and CloudTrail. It simplifies the process by automatically configuring integration across the root account and all associated sub-accounts within the specified organizational unit (OU). Additionally, it creates an SNS topic and Lambda function, ensuring that any new AWS accounts added to the organization are seamlessly integrated with Lacework.
The module will perform the following tasks:
- Create the CloudTrail integration at the root account level.
- Create AWS Configuration integration for each of the sub-accounts. Note that this is not the same as the AWS Config service. Lacework does not rely on the native AWS Config service.
For Lacework to access configurations in the AWS sub-accounts, the aws_org_configuration module creates the necessary IAM roles inside those sub-accounts using CloudFormation templates. These IAM roles are assumed by Lacework to read the AWS configuration.
Usage:
Using the module is straightforward. Below is the basic configuration needed. It is highly recommended to use variables to pass secrets.
provider "aws" {
region = "us-west-2"
}
module "aws_org_configuration" {
source = "lacework/org-configuration/aws"
version = "~> 0.1"
cf_resource_prefix = "lw"
lacework_access_key_id = var.key_id
lacework_account = var.lw_account
lacework_secret_key = var.secret_key
organization_id = "o-XXXXXX"
organization_unit = "r-xxxxx"]
}Running terraform state list after the deployment should show the following resources:
% terraform state list
module.aws_org_configuration.data.archive_file.lambda_zip_file
module.aws_org_configuration.data.aws_caller_identity.current
module.aws_org_configuration.data.aws_iam_policy_document.kms_key_policy
module.aws_org_configuration.data.aws_iam_policy_document.lacework_copy_zip_files_assume_role
module.aws_org_configuration.data.aws_iam_policy_document.lacework_copy_zip_files_role
module.aws_org_configuration.data.aws_iam_policy_document.lacework_setup_function_assume_role
module.aws_org_configuration.data.aws_iam_policy_document.lacework_setup_function_role
module.aws_org_configuration.data.aws_iam_policy_document.sns_topic_policy
module.aws_org_configuration.data.aws_partition.current
module.aws_org_configuration.data.aws_region.current
module.aws_org_configuration.aws_cloudformation_stack.lacework_stack
module.aws_org_configuration.aws_cloudformation_stack_set.lacework_stackset
module.aws_org_configuration.aws_cloudformation_stack_set_instance.lacework_stackset_instances
module.aws_org_configuration.aws_iam_role.lacework_copy_zip_files_role
module.aws_org_configuration.aws_iam_role.lacework_setup_function_role
module.aws_org_configuration.aws_kms_key.lacework_kms_key_0]
module.aws_org_configuration.aws_lambda_function.lacework_copy_zip_files
module.aws_org_configuration.aws_lambda_function.lacework_setup_function
module.aws_org_configuration.aws_lambda_invocation.lacework_copy_zip_files
module.aws_org_configuration.aws_lambda_permission.lacework_lambda_permission
module.aws_org_configuration.aws_s3_bucket.lacework_org_lambda
module.aws_org_configuration.aws_s3_bucket_ownership_controls.lacework_org_lambda
module.aws_org_configuration.aws_s3_bucket_public_access_block.lacework_org_lambda
module.aws_org_configuration.aws_s3_bucket_versioning.lacework_org_lambda
module.aws_org_configuration.aws_secretsmanager_secret.lacework_api_credentials
module.aws_org_configuration.aws_secretsmanager_secret_version.lacework_api_credentials
module.aws_org_configuration.aws_sns_topic.lacework_sns_topic
module.aws_org_configuration.aws_sns_topic_policy.default
module.aws_org_configuration.aws_sns_topic_subscription.lacework_sns_subscription
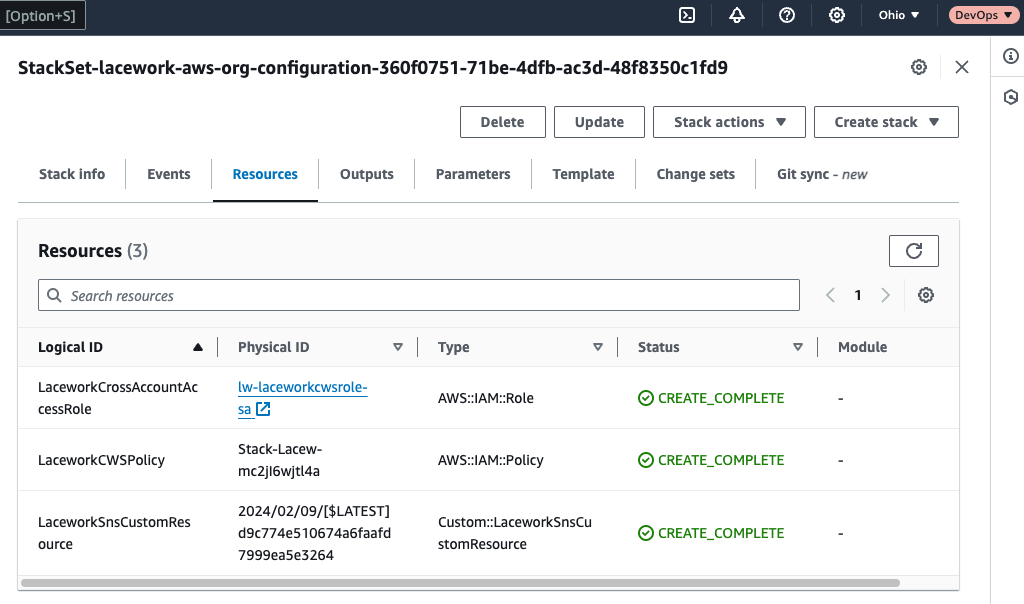
In addition, at every sub-account configured, you should see the following Cloudformation stack:
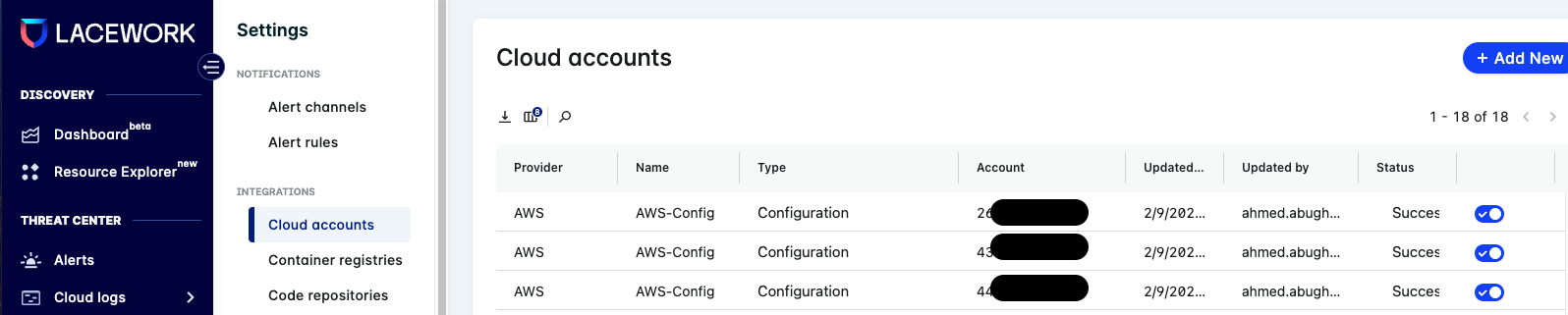
Once the integration is successful, you should be able to see your accounts under the Settings→ Cloud Accounts:
References:
- https://registry.terraform.io/modules/lacework/org-configuration/aws
- https://docs.lacework.net/onboarding/aws-integration-terraform-any-supported-host
Agent
N/A
Platform
Deploy Lacework/Installation
Cloud
AWS
