General Instructions for setup:
- Complete the steps in the following documentation in order to set up an App Integration in Okta with all the Lacework Service Provider information.
- Note: In following the above instructions make sure to add the following required attribute statements to the App Integration for JIT access:
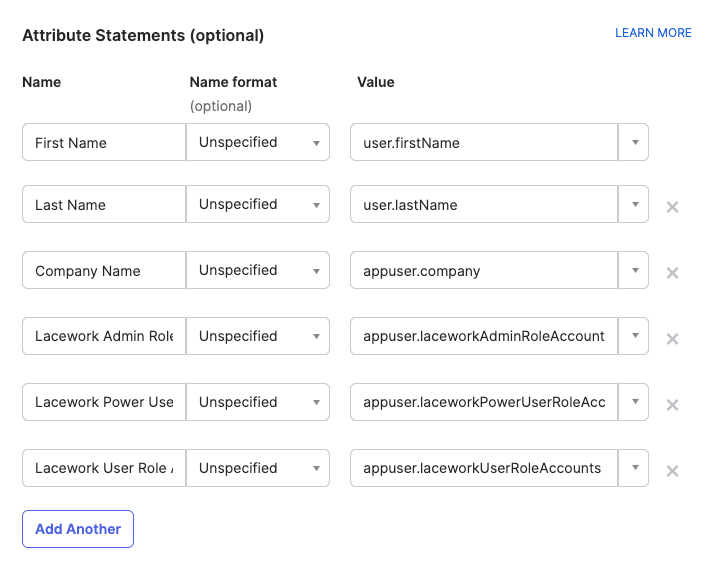
-
If you are using a Lacework Organization with multiple accounts, additional attribute statements must also be added for Organization level roles.
-
Lacework Organization Admin Role
-
Lacework Organization User Role
-
-
For more information about attribute statements, reference the following documentation: https://docs.lacework.net/onboarding/configure-saml-jit-with-okta
- Note: In following the above instructions make sure to add the following required attribute statements to the App Integration for JIT access:
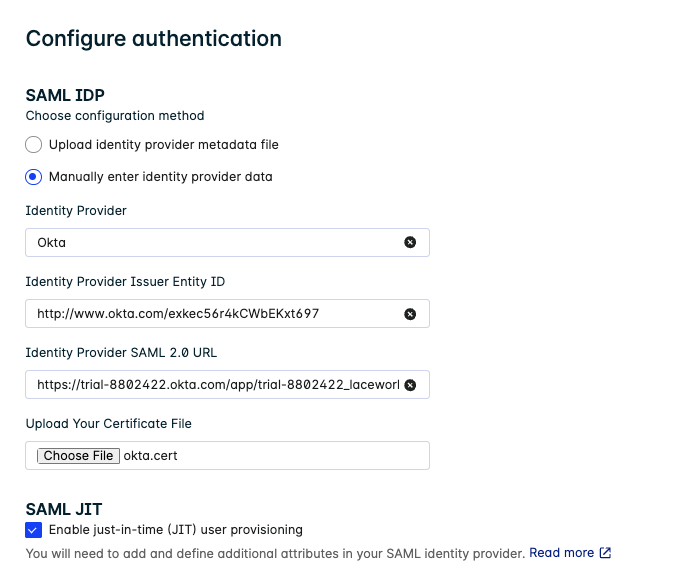
- Once the App integration is created in Okta with all the correct attribute statements, select the "View SAML setup instructions" option to view the SAML app details.
- Log back into lacework and add these IDP metadata details to the Lacework Authentication page.
- Navigate back to Okta and add attributes to your newly created Lacework App so that the attribute values can be populated at the group level.
- Navigate to Directory > Profile Editor and select Apps > Lacework User
- Add the following custom attribute mappings to the Lacework Application Profile:
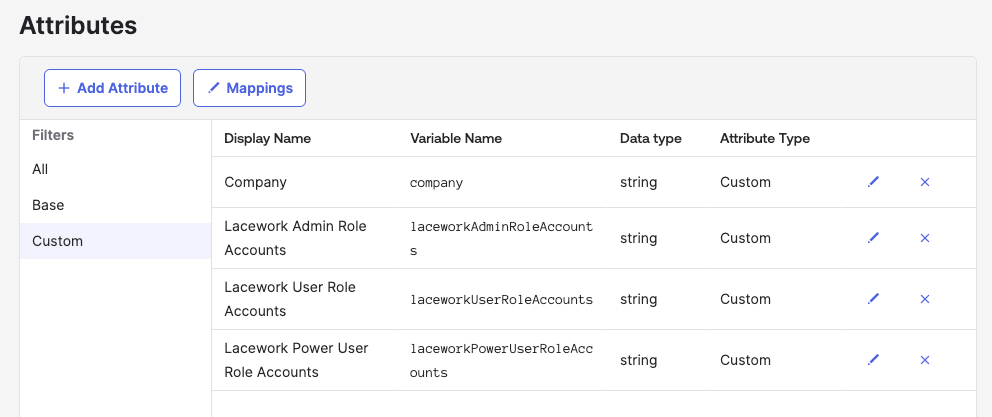
- Note that the "Attribute type" for each mapping should be set to “Group” if you want to manage these values at the group level compared to managing per user.
- Additionally “Lacework Organization Admin Role” and “Lacework Organization User Role” attributes will need to be added here as well if you are using a Lacework Organization.
- Assign the Lacework App to the specific Okta groups that require access. Once that Application is assigned, make sure to modify the attribute values of the assignment to match the needs of your organization. If these values are not modified, they will default to null.
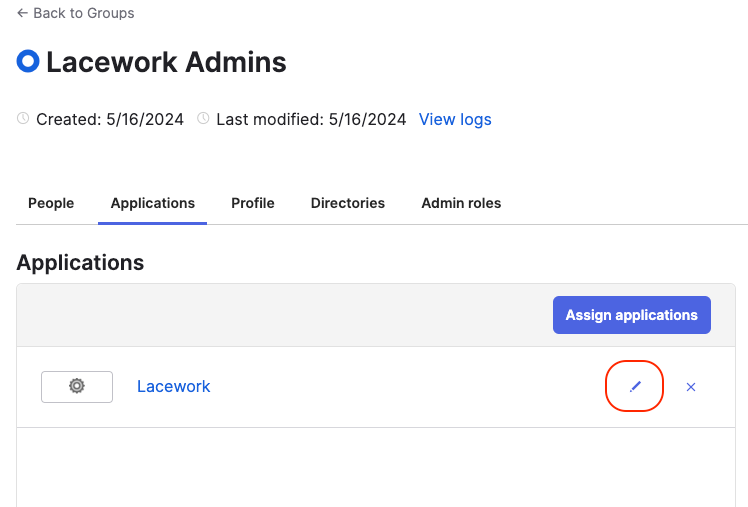
Architecture Recommendations for Lacework User and Group management in Okta:
- Manage Lacework users at the group level so that attribute values can be set once compared to setting them for each individual user which can be a manual burden on Okta admins.
- Separate groups in Okta by different roles in the Lacework platform: Admin, Read-only, Power User, etc. Then for each Okta group set only set one of the Lacework attribute values to “*” while leaving the rest of the fields blank. This modification will enable all the users in this group to only have one specific role in the Lacework platform. For example, if we want to have a Lacework Power Users Okta group, the values of each attribute should be as follows:
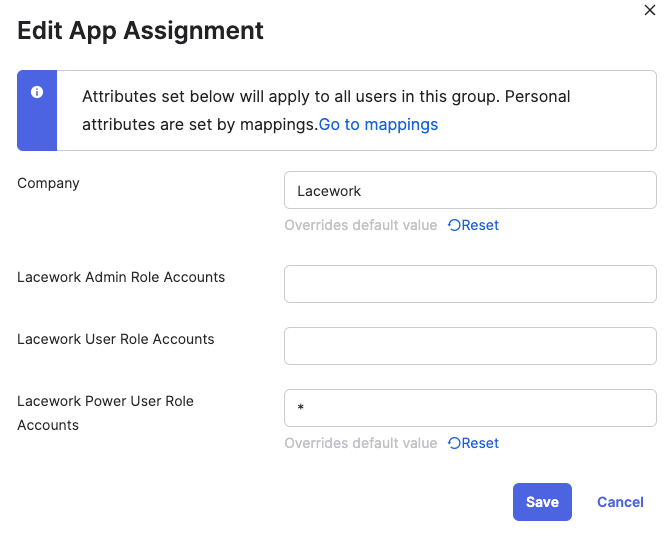
- Consider creating Custom User Groups in Lacework for more fine grained access control in addition to the Lacework default roles. For most information on how to create custom role and user groups in lacework reference the following documentation: https://docs.lacework.net/onboarding/manage-access-account-level
Troubleshooting:
Reference the following community post for troubleshooting SAML JIT issues:
Agent
N/A
Platform
Deploy Lacework/Installation
Cloud
N/A
