Introduction:
Are you trying to configure your Lacework Instance to use SAML JIT and getting the following message?
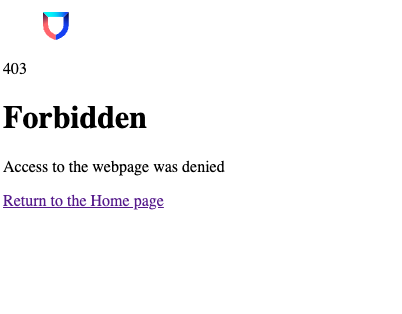
Well it turns out you’re not the only one, and even better it’s probably going to be a pretty easy fix!
Typically 403s are a result of not having your JIT attributes configured properly - e.g. they’re not included when expected, attribute names are mis-typed or maybe the values you’re assigning can’t be determined in the platform (e.g. incorrect account names).
JIT Attribute Recap:
In order for a user to gain access to the Lacework Platform they must have the following attributes set against their profile/group in your IDP:
- First Name
- Last Name
- Company
- Lacework Admin Role Account OR Lacework Power User Role Accounts OR Lacework User Role Accounts (they only need one of these attributes - but Lacework will choose the highest level of access included)
For the full list (and what values you can include), check out the full documentation here.
How to Troubleshoot:
The first thing you’re going to want to do is install a SAML Inspector into your browser of choice - for this guide I’m using Google Chrome and the extension is SAML Chrome Panel.
Once you have this installed use the following steps to debug the issue:
- Open Developer Tools in your browser
- You should now see a SAML tab in line with Elements, Console, Sources, Network etc…
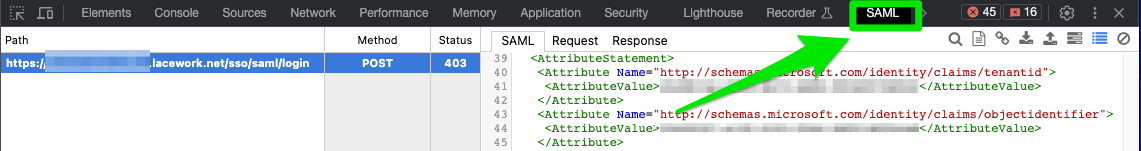
- Re-submit your login request (just a reload here should do)
- Check the SAML Attribute Payload that has been sent:
(For the record, I’m using Azure AD, but this guide should be usable regardless of IDP.)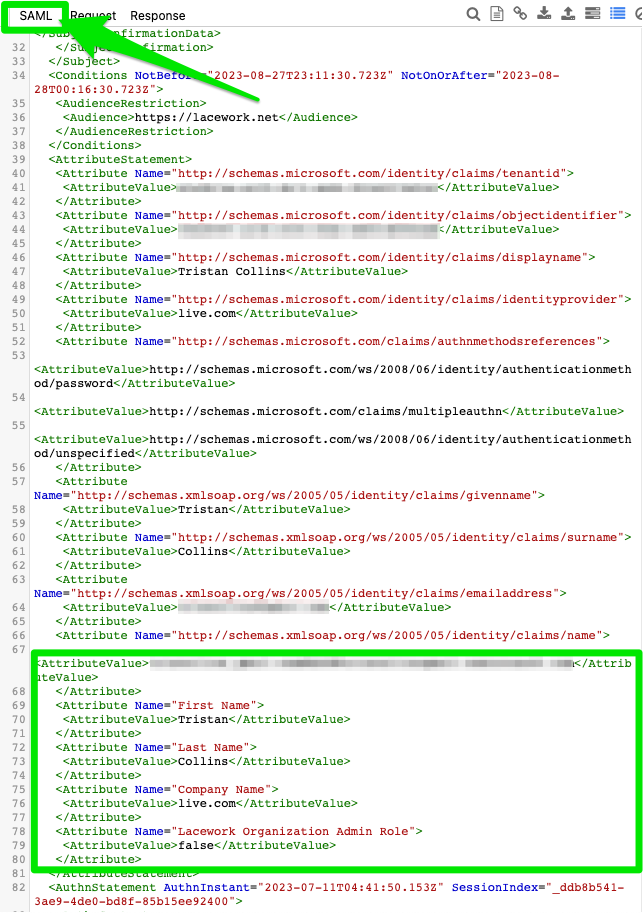
As you can see I’ve forgotten to include my Role Attribute (Admin, Power User, User)!!
-
Make the required adjustments in your IDP and try to log in again (NOTE - you may need to close and reopen your browser, clear your cache etc etc)
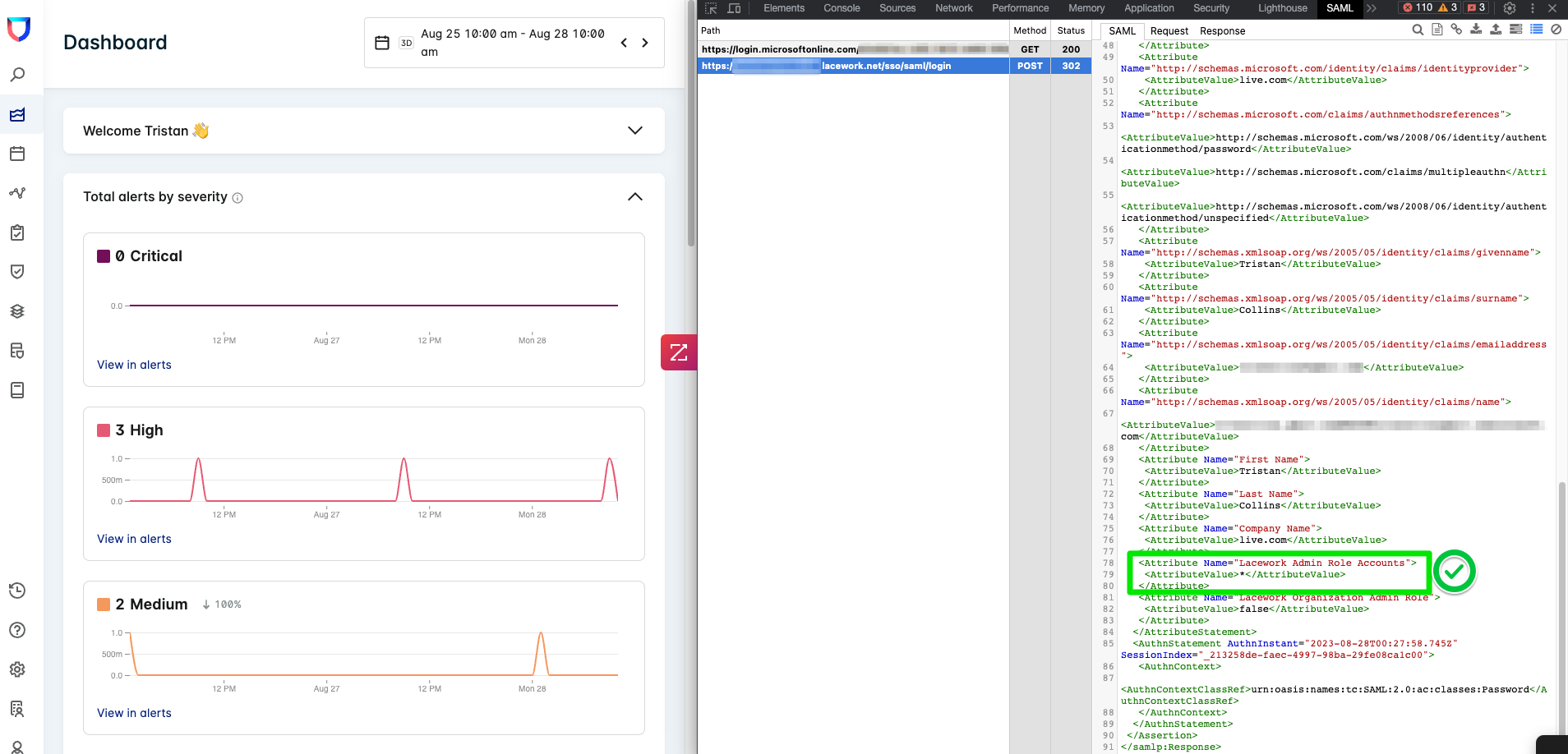
TA DA!
Of course - if this guide does not resolve your issue - please contact our support team (https://support.lacework.com).
Please include screen shots of the SAML Inspector in your ticket as this will help your engineer!
Agent
N/A
Platform
Current
Cloud
N/A
